IT-Security and Onions
In IT security, we often talk about the onion principle. And even though many infrastructures can truly bring tears to your eyes – that’s not what the term refers to in this case.
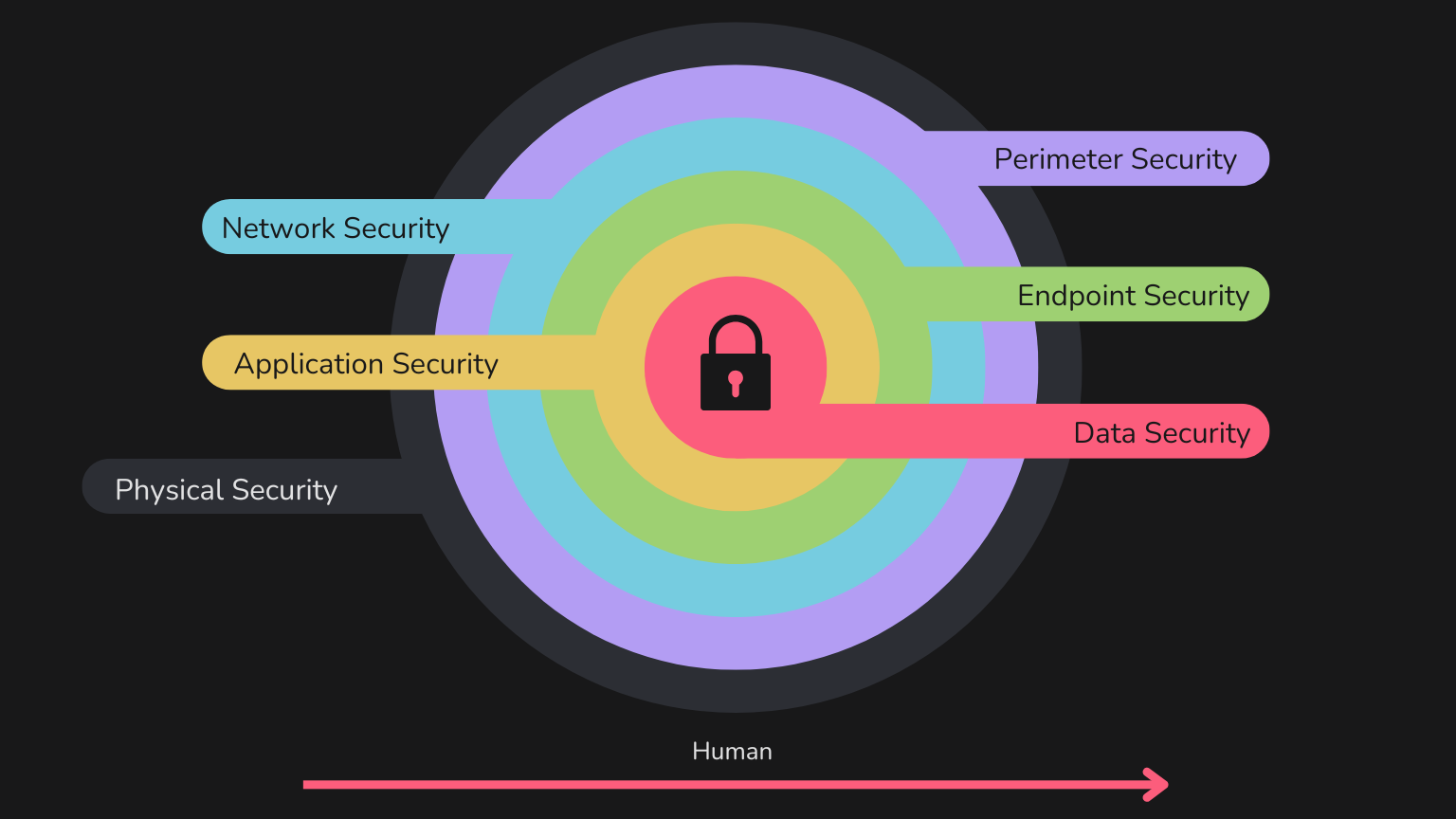
What’s meant is the approach of viewing IT security in multiple layers: each layer protects a different part of the system. In this model, redundancies are not only accepted – they are encouraged. True security comes from depth, not from isolated measures.
Depending on who you ask, the models may vary slightly. We’ve grouped the layers thematically – with a short digression on a frequently underestimated aspect:
The Human Factor
We humans use different mechanisms to determine if something is wrong, starting with our senses: visual signals, smells, sounds. If we smell something burning, we know either to quickly take something off the stove or hope, upon returning home, that the smell isn’t coming from our own apartment.
In the digital world, our senses and learned responses don’t work so well in critical situations, so we must train ourselves to recognize risks quickly here as well. The human factor isn’t really its own layer, but measures in other layers won’t be effective if users aren’t trained—or worse, work against them.
Physical Security
The first layer of protection begins offline: devices, network interfaces, server rooms, or entire data centers must be physically secured. Unsupervised access by an attacker can potentially bypass all digital protections.
Example: Someone shows up to “service the printer,” but no appointment was scheduled. Every employee should become suspicious and check with the responsible IT personnel to verify.
Perimeter Security
The outermost digital line of defense: firewalls, web application firewalls, IDS/IPS systems (Intrusion Detection & Prevention). Important: These systems must be regularly updated, and alerts must be taken seriously – a forgotten shield offers no protection.
Network Security
If an attacker does manage to enter the network, they must not be able to move freely. This is where network segmentation comes into play – it limits movement and makes it much harder to exploit further vulnerabilities.
Endpoint Security
Our work devices also need to be secured, although I’m not a fan of antivirus software. These programs have extensive privileges, increasing the attack surface, and their deep integration into the OS can lead to problems (e.g., system fails to boot). But there are other important aspects of endpoint security: access control, patch and update management, and permissions management.
Application Security
Many applications now run remotely or in the cloud – direct access is missing. Therefore: set network rules correctly, monitor data flows, and isolate suspicious behavior.
If the application is self-hosted or developed in-house, additional measures apply: Secure Development Lifecycle, access management, and continuous patching are mandatory.
Data Security
The core of the onion – the sacred data, the very thing we aim to protect. Think of it like the contents of a safe (physical security, keycards, biometric sensors, time-based access restrictions – multiple security factors and layered measures) or the inside of our homes (various locks, alarm systems).
Here it’s important to plan for the failure of other layers: data encryption, backup strategies, and incident response plans – which must be tested in case something goes wrong.
Conclusion
The approach of breaking down complex topics into layers is used in many fields, especially where security and reliability are key.

Security is not a product, but a process – and a layered one at that. The onion principle helps us think through this process systematically.
At RiKuWe, we integrate IT security into our concepts and are happy to discuss your individual needs in an initial consultation. We look forward to your inquiry!
And finally: Don't rely on just one measure and then feel safe – it's best to build your own onion (😉).
